
Data Protection | CBSE Class 11 | Computer Science
Dear Class 11th STUDENTS, !
Welcome to this tutorial of Data Protection from your CBSE class 11 of Computer Science Syllabus .
In this tutorial, we shall be learning our chapter-3: Data Protection from Unit 3: Society, Law and Ethics (SLE-1)- Cyber safety as CBSE BOARD suggested to learn about computer system and its organisation to complete this section.
Unit 3: Society, Law and Ethics (SLE-1)- Cyber safety
- Data Protection:
- Intellectual property rights (copyright, patent, trademark),
- Violation of IPR (plagiarism, copyright infringement, trademark infringement),
- Opensource software and licensing (Creative Commons, GPL and Apache)
I advice you to check the latest syllabus given by CBSE Board at its Official website: www.cbseacademic.nic.in
Also, in this tutorial we will covers all necessary topics/concepts required to complete your exams preparations in CBSE classes 11th.
NOTE:
- We are also giving some important Questions & Answers for better understanding as well as preparation for your examinations.
- You may also download PDF file of this tutorial from our SHOP for free.
- For your ease and more understanding, we are also giving the video explanation class of each and every topic individually, so that you may clear your topics and get success in your examinations.

Introduction
We are now living an era which is called the information age where we see that most our activities are technology-influenced, be it making an online payment, creating or development of own piece of art or information (such as writing articles or clicking photographs and so forth). With the reach of technology to our day life, there has been a paradigm shift, and it has also raised specific issues and problems related to society, ethics and law. In this chapter, we shall talk about topics about this very domain such as intellectual property rights, plagiarism, cybercrime, cyberlaw, e-waste management etc.
Data Protection
Data protection refers to the processes and measures implemented to safeguard sensitive information from unauthorized access, loss, or corruption. It encompasses a range of strategies and technologies designed to ensure data privacy, integrity, and availability throughout its lifecycle.
On other hand Data protection signifies the strategic and procedural steps undertaken to safeguard the privacy, availability, and integrity of sensitive data, and is often interchangeably used with the term ‘data security.’
Data privacy is a guideline for how data should be collected or handled, based on its sensitivity and importance. Data privacy is typically applied to personal health information (PHI) and personally identifiable information (PII). This includes financial information, medical records, social security or ID numbers, names, birthdates, and contact information.
Key aspects of data protection include:
Data Security:
Protecting data from unauthorized access, modification, or deletion through measures like encryption, access controls, and firewalls.
Data Privacy:
Ensuring the confidentiality and security of personal information, often through compliance with regulations like GDPR and CCPA.
Data Backup and Recovery:
Implementing strategies to back up data and restore it in case of loss or damage, ensuring business continuity.
Data Erasure:
Deleting data that is no longer needed, sometimes as a requirement of data privacy regulations.
Why is data protection important?
Data protection or Privacy is essential for following reasons :
- Preventing Data Breaches: Data protection measures help mitigate the risk of data breaches, which can lead to financial losses, reputational damage, and legal penalties.
- Complying with Regulations: Many regulations, such as GDPR and CCPA, mandate specific data protection practices to protect personal information.
- Maintaining Customer Trust: Strong data protection practices demonstrate a commitment to protecting sensitive information, which can build trust with customers and stakeholders.
- Ensuring Business Continuity: Data protection strategies help ensure that businesses can continue operating even in the event of data loss or corruption.
Ethical Issues
These days, we can easily say that our society is information society and our era is information era. As we all know that information is the means to acquire Knowledge. In other words, we can say that information forms the intellectual capital for a person or body. However, there are many ethical issues involved with the usage and availability of information.
Some common ethical issues are:
- Intellectual property rights
- Plagiarism
- Digital property rights
Intellectual Property Rights
As mentioned earlier, information makes intellectual property. Any piece of information is produced or created with a lot of efforts and it consumes a lot of time. The cost factor is also involved with the creation or production of information. Though once produced, it becomes very easy to duplicate it or share it with others. But this very thing makes information difficult to safeguard unlike tangible property.
The creator/producer of the information is the real owner of the information. And the owner has every right to protect his|her intellectual property. To protect one’s intellectual property rights one can, get information copyrighted or patented or use trademarks.
The ethical issue involved with it is that information must not be exchanged without the consent of its owner.
The intellectual property rights must be protected, for it:
- Encourages individuals and businesses to create new software and new software applictions, as well as improving existing applications,
- Ensures new ideas and technologies are widely distributed,
- Promotes investment in the national economy.
Types of Intellectual Property Rights:
Patents
Protect inventions, granting the inventor the exclusive right to make, use, and sell their invention.
Copyright
Protect original works of authorship, such as books, music, and software, granting the creator exclusive rights to reproduce, distribute, and display their work.
Trademarks
Protect brand names and logos used on goods and services, allowing businesses to distinguish their products from others.
Violation of IPR (Intellectual Property Rights)
Plagiarism
Simply put, plagiarism means stealing. Surprised? If you look into an English dictionary to find the meaning of word plagiarism, it will give somewhat like “the unauthorized use or close imitation of the language and thoughts of another author and the representation of them as one’s own original work.’’
Thus, Plagiarism is stealing someone else’s intellectual work (can be an idea, literary work or academic work etc.) and representing it as your own work without giving credit to creator or without citing the source of information.
Any of the following acts would be termed as Plagiarism:
- Using some other author’s work without giving credit to the author.
- Using someone else’s work in incorrect form than intended originally by the author/creator.
- Modifying/lifting someone’s production such as music-composition etc. Without attributing it to the creator of the work
- Giving incorrect or incorrect source of information i.e., wrongful citation.
- Failure in giving credit or acknowledging the contribution of others in a collaborative effort, to which you are also part of.
How not to plagiarize
As most universities1 put in their student-handbook. ‘To avoid plagiarism:
- Another person’s idea, opinion, or theory;
- Quotations of another person’s actual spoken or written words; or
- Paraphrase of another person’s spoken or written words.
Plagiarism is Offence
‘if plagiarism involves copying not only ideas but also a substantial portion of a copyrighted work without attribution and without permission, it would amount to both copyright infringement and the violation of the ‘special right’ of the author to be credited.
Copyright infringement and the violation of an author’s right be credited are both civil wrongs and criminal offences. A civil suit may be instituted, and criminal charges may also field’2.
Both civil suit and criminal charges are punishable offences and amount to fine and penalties.
Copyright infringement:
Copyright infringement is the unauthorized use, reproduction, or distribution of someone else’s creative work without permission from the copyright holder. This applies to various content, such as images, text, music, or software, and can lead to legal consequences, even for unintentional use. Simply taking content from the internet or not giving proper credit can be a violation of copyright.
- It’s the unauthorized use of someone else’s original work that is protected by copyright law.
- This includes actions like reproducing, distributing, publicly displaying, or creating derivative works from copyrighted material.
Examples relevant to a Copyright infringement
- Using images in projects:
Downloading an image from the internet and using it in your project without the owner’s permission is a copyright infringement, even if you mention the source.
- Sharing copyrighted content:
Posting entire episodes of a TV show on a platform like YouTube without authorization infringes on the original creators’ copyright.
- Copying text from books or websites:Reproducing significant portions of a copyrighted work without consent, even if you cite it, can also be an infringement.
Trademark infringement:
Trademark infringement refers to the unauthorized use of a registered trademark, or a deceptively similar mark, that creates confusion or deceives the public into believing there’s a connection to the actual trademark owner. This violates the exclusive rights granted by the Trademark Act 1999, leading to potential legal actions, financial penalties, and even imprisonment for the infringer. It is the violation of exclusive rights for a registered trademark under the Indian Trademarks Act, 1999.
- Unauthorized Use: A person or company uses a trademark without permission from the registered owner.
- Deceptively Similar: The used mark is identical or so similar to the registered trademark that it causes consumers to be confused.
- Confusion: The infringement leads the public to believe that there is an official connection between the infringer’s goods/services and the trademark owner’s.
Digital Property Rights
Digital property (or digital assets) refers to any information about you created by you that exists in digital form, either online or an electronic storage device. All of your digital property comprises what is known as your digital estate.
Examples of digital property include: any online personal accounts, such as email and communications accounts, social media accounts, shopping accounts, photo and video sharing accounts, video gaming accounts, online storage accounts, and websites and blogs that you manage; domain names registered in your name; intellectual property, including copyrighted materials, trademarks, patents and any software or code (such as software tools created by you or games or apps created by you) you may have written and own etc.
Digital Property rights lie with the owner. Legally a person who has created it of r the owner who has got it developed by paying legally is the legal owner of a digital property. Only the owner can use and decide who all and in what form can/her digital asset may be used by other, whether by making payments or by buying it or by obtaining its license or usage rights etc. But this is not the case generally; there are many threats to digital properties.
Open Source Philosophy and Software Licenses
Broadly the term ‘open source software’ is used to refer to those categories of software/ programs whose licenses do not impose much conditions. Such software, generally give users freedom to run/use the software for any purpose, to study and modify the program, and to redistribute copies of either the original or modified program (without having to pay royalties to pervious developers).
There are many categories of software that may be referred to as open software.
Following subsection is going to talk about the same.
Terminology
Before we talk about various terms and definitions pertaining to ‘Open’ world, you must be clear about two terms which are often misunderstood or misinterpreted. These terms are:
Ø Free software and
Ø Open source software
Free software
Free software means the software is freely accessible and can be freely used, changed, improved, copied and distributed by all who wish to do so. And no payments are needed to be made for free software.
The definition of free software is published by Richard Stallman’s Free software Foundation. Here is the key text 3 of that definition

Open Source Software
Open source software, on the other hand, can be freely used (in terms of making modifications, constructing business models around the software and so on ) but it does not have to be free of charge. Here the company constructing the business models around open source software may receive payments concerning support, further development. What is important to Know here is that in open source software, the source code is freely available to the customer.
Philosophy of Open Source
It states that:
Open source doesn’t just mean access to the source code. The distribution terms of open-source software must comply with the following criteria:
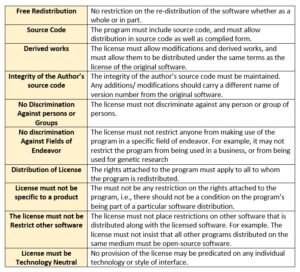
A software which is free as well as open belongs to category FOSS (free and open software).
Open – source licenses
Open – source licenses make it easy for others to contribute to a project without having to seek special permission. It also protects you as the original creator, making sure you at least get some credit for your contributions. It also helps to prevent others from claiming your works as their own.
Broadly used open source licenses are being given below for your reference:
1. GNU General Public License (GPL)
The GNU General Public License (GPL) is probably one of the most commonly used licenses for open-source projects. The GPL grants and guarantees a wide range of rights to developers who work on open- source projects. Basically, it allows users to legally copy, distribute and modify software. This means, with GPL, a user can:

Apache License
The Apache License, grants a number of rights to users. These rights can be applied to both copyrights and patents. The Apache License offers:

Redistributing code requires giving proper credit to contributors to the code and the same license (Apache) would remain with the software extension.
How to Safeguard User Privacy
To ensure that the user privacy is not compromised, following measures must be taken:
- The merchant or the seller must clearly state about how the user data will be used, in the terms and conditions of its site application.
- The merchant or seller must ensure that the user has gone through the terms and conditions given on its site application prior to making any transactions.
- The merchant must assure the user about data safety by implementing proper data safety and security measures such as https protocol and other security mechanism so that users; data is safe from hackers too.
- The user must go through the terms and conditions of the seller/ merchant site before providing any sensitive information and make sure that the site is a safe site by checking https protocol and padlock etc.



